Configure SOHO Networks
Introduction: Configure SOHO Networks
The OSI model involves quite a lot of abstraction. As a practical example, it is worth examining how a basic network is implemented. In this topic, you will learn the connection and configuration options for components within a typical small office/home office (SOHO) router.
SOHO Routers
Networks of different sizes are classified in different ways. A network in a single location is often described as a local area network (LAN). This definition encompasses many different sizes of networks with widely varying functions and capabilities. It can include both residential networks with a couple of computers, and enterprise networks with hundreds of servers and thousands of workstations.
Small office/home office (SOHO) is a category of LAN with a small number of computing hosts that typically rely on a single integrated appliance for local and Internet connectivity.
Networks such as the Internet that are located in different geographic regions but with shared links are called wide area networks (WANs). The intermediate system powering SOHO networks is usually described as a SOHO router because one of its primary functions is to forward traffic between the LAN and the WAN. However, routing is actually just one of its functions. We can use the OSI model to analyze each of these in turn.
Physical Layer Functions
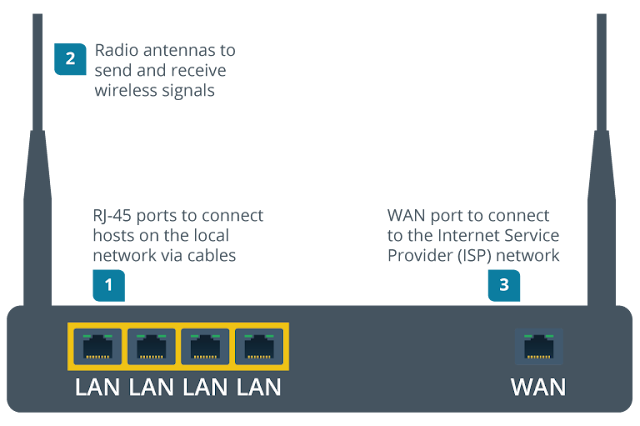
Starting at layer 1, the SOHO router provides the following physical connections:
- A number of RJ-45 ports (typically four) to connect to a local cabled network. These are typically labeled as the LAN ports.
- Radio antennas to transmit and receive wireless signals.
- A type of modem (typically cable or digital subscriber line) to connect to the Internet Service Provider's (ISP's) network. This is typically labeled as the WAN port. On the example in the diagram, the interface is another RJ-45 port, designed to connect to a fiber to the premises Internet service using the same Ethernet technology as the local network. On other SOHO routers, there may be a different type of WAN modem, such as an RJ-11 port to connect to a digital subscriber line (DSL) service.
Physical layer connectivity options on a SOHO router.
Data Link Layer Functions
At layer 2, the SOHO router implements the following functions to make use of its physical layer adapters:
- Ethernet switch-the RJ-45 jacks are connected internally by an Ethernet switch.
- Wireless access point-the radio antennas implement some version of the Wi-Fi standard. The access point functions as a wireless hub, allowing stations (PCs, tablets, smartphones, and printers) to form a wireless network. The access point is also wired to the Ethernet switch via an internal port. This forms a bridge between the cabled and wireless segments, creating a single logical local network.
Data link layer local network segment. (Images © 123RF.com)
At this layer, each host interface is identified by a media access control (MAC) address.
Network Layer Functions
At layer 3, the network layer, the routing part of the SOHO router makes forwarding decisions between the local private network and public Internet. These zones are distinguished by internet protocol (IP) addresses. The local network uses a private IP address range, such as 192.168.1.0/24. The SOHO router itself is identified by an address in this range, such as 192.168.1.1 or 192.168.1.254 .
Network layer private and public segments. (Images © 123RF.com)
The router runs a dynamic host configuration protocol (DHCP) server to allocate a unique address to each host that connects to it over either an Ethernet port or via the wireless access point. The addresses assigned to clients use the same first three octets as the router's address: 192.168.1. The last octet can be any value from 1 to 254, excluding whichever value is used by the router.
Configuring the LAN addresses using DHCP on a wireless router. (Screenshot courtesy of TP-Link Technologies Co., Ltd.)
The SOHO router's WAN interface is allocated a public IP address, say 203.0.113.1, by the internet service provider. When a host on the local network tries to access any valid IP address outside the 192.168.1.0/24 range, the router forwards that packet over its WAN interface and directs any replies back to the host on the LAN.
Configuring the WAN (internet) interface on a wireless router. These parameters are supplied by the ISP. Many ISP services use DHCP to allocate a dynamic WAN address, but some offer static addressing. (Screenshot courtesy of TP-Link Technologies Co., Ltd.)
Transport and Application Layer and Security Functions
There is no separate OSI model layer for security. Instead, security issues can arise and solutions are needed at every layer. Network security is essentially a matter of allowing or preventing devices, users, and services (applications) from using the network. The WAN interface is the network perimeter. The SOHO router can apply filtering rules to traffic sent between the public and private zones, implementing a firewall. The firewall can be configured to block traffic based on source or destination IP addresses and also on the type of application.
At layer 4, each application is identified by a port number, such as 80 for hypertext transfer protocol (HTTP) web traffic or 25 for Simple Mail Transfer Protocol (SMTP) email traffic.
The firewall in the router can be configured with rules specifying behavior for each port. For example, computers on the network might use the server message block (SMB) protocol to share files. It would not be appropriate for hosts on the Internet to be able to access these shared files, so the SMB port would be blocked by default on the WAN interface but allowed on the LAN and WLAN interfaces.
Any host can connect to the RJ-45 ports on the router and join the network. The wireless network is usually protected by an encryption system that requires each station to be configured with a passphrase-based key to join the network.
Access to the router's management interface and its configuration settings is protected by an administrative account passphrase. As the router is connected to the Internet, it is critical to configure a strong passphrase.
The Internet
The WAN interface of the router connects the SOHO network to the Internet.
The Public Switched Telephone Network
Most SOHO subscriber Internet access is facilitated via the public switched telephone network (PSTN). The SOHO router is described as customer premises equipment (CPE). More widely, this is any termination and routing equipment placed at the customer site. Some of this equipment may be owned or leased from the telecommunications company (or telco); some may be owned by the customer.
The CPE is connected via its modem and WAN port to the local loop. This is cabling from the customer premises to the local exchange. The point at which the telco's cabling enters the customer premises is referred to as the demarcation point (often shortened to demarc).
Internet Service Providers
The major infrastructure of the Internet consists of high bandwidth trunks connecting Internet eXchange Points (IXPs). Within an IXP datacenter, ISPs establish links between their networks, using transit and peering arrangements to carry traffic to and from parts of the internet they do not physically own. There is a tiered hierarchy of ISPs that reflects to what extent they depend on transit arrangements with other ISPs.
Internet Standards
Although no single organization owns the Internet or its technologies, several organizations are responsible for the development of the internet and agreeing common standards and protocols.
- Internet Assigned Numbers Authority (IANA) ( iana.org )-manages allocation of IP addresses and maintenance of the top-level domain space. IANA is currently run by Internet Corporation for Assigned Names and Numbers (ICANN). IANA allocates addresses to regional registries who then allocate them to local registries or ISPs. The regional registries are Asia/Pacific (APNIC), North America and Southern Africa (ARIN), Latin America (LACNIC), and Europe, Northern Africa, Central Asia, and the Middle East (RIPE NCC).
- Internet Engineering Task Force (IETF) ( ietf.org )-focuses on solutions to Internet problems and the adoption of new standards, published as Requests for Comments (RFCs). Some RFCs describe network services or protocols and their implementation, while others summarize policies. An older RFC is never updated. If changes are required, a new RFC is published with a new number. Not all RFCs describe standards. Some are designated informational, while others are experimental. The official repository for RFCs is at rfc-editor.org .
References to RFCs in this course are for your information should you want to read more. You do not need to learn them for the certification exam.
The OSI model has a stricter definition of the Session, Presentation, and Application layers than is typical of actual protocols used on networks. The Internet model (tools.ietf.org/html/rfc1122) uses a simpler four layer hierarchy, with a link layer representing OSI layers 1 and 2, layer 3 referred to as the Internet layer, a Transport layer mapping approximately to layers 4 and 5, and an Application layer corresponding to layers 6 and 7.
Hexadecimal Notation
To interpret network addresses, you must understand the concept of base numbering systems. To start with the familiar; decimal numbering is also referred to as base 10. Base 10 means that each digit can have one of ten possible values (0 through 9). A digit positioned to the left of another has 10 times the value of the digit to the right. For example, the number 255 can be written out as follows:
(2x10x10)+(5x10)+5
Binary is base 2, so a digit in any given position can only have one of two values (0 or 1), and each place position is the next power of 2. The binary value 11111111 can be converted to the decimal value 255 by the following sum:
(1x2x2x2x2x2x2x2)+(1x2x2x2x2x2x2)+(1x2x2x2x2x2)+(1x2x2x2x2)+(1x2x2x2)+(1x2x2)+(1x2)+1
As you can see, it takes 8 binary digits to represent a decimal value up to 255. This number of bits is called a byte or an octet. The four decimal numbers in the SOHO router's WAN IP address 203.0.113.1 are octets.
While computers process everything in binary, the values make for very long strings if they have to be written out or entered into configuration dialogs. Hexadecimal notation (or hex) is a convenient way of referring to the long sequences of bytes used in some other types of network addresses. Hex is base 16 with the possible values of each digit represented by the numerals 0 through 9 and the characters A, B, C, D, E, and F.
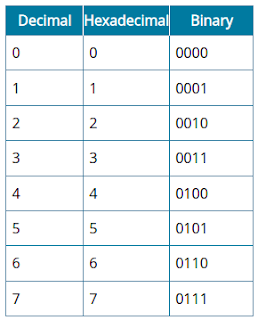
Use the following table to help to convert between decimal, binary, and hexadecimal values.
As you can see from the table, every hex digit lines up neatly with four binary digits (a nibble). Each byte or octet can be expressed as two hex digits. For example, the decimal value 255 is FF in hex. This would sometimes be written as 0xFF for clarity.
Example Exam :
1. Which of the following OSI model layers will discard a segment with a bad checksum in the UDP header?
Transport
2. Which the following devices have capability to allow communication between two different subnetworks?
Router
3. A security engineer implements port security on a hardware firewall. Which OSI model layer identifies the application ports to configure?
Layer 4
4. Which of the following is used to provide networking capability for VMs at Layer 2 of the OSI model?
vSwitch
5. An application developer is attempting to troubleshoot issues with ASCII conversion for their application At wich layer of the OSI model are they troubleshooting
Presentation







Posting Komentar untuk "Configure SOHO Networks"